The road to a successful cyberattack often leads through an organization’s employees, since they already have authenticated access (perhaps to highly sensitive data), and they have intimate knowledge of the organization, its people, processes, and technology.
Sometimes, attackers use employees unwittingly, deploying social engineering to trick them into providing access. Other times, insiders knowingly partner with external attackers, selling access or data for cash. Insider threats have impacted a number of worldwide brands–one of the most noteworthy being healthcare firm Bupa where an employee stole data belonging to over 500,000 customers from its CRM system and attempted to sell it on the dark web. Similarly, in 2021, authorities charged an employee at a large telecom company for providing SIM swaps to threat actors for $500 apiece.
Insiders can also willingly share sensitive and proprietary data when motivated by ideological reasons. Recently, two Tesla employees leaked data about self-driving features to a German newspaper. The shared data also included personal information of over 75,000 Tesla customers.
Considering that the deep and dark web are anonymous by design, it is a fitting venue for those seeking to find malicious insiders. Upon investigation, we were not disappointed. This report discusses our findings and details how organizations can protect themselves from a broad variety of insider threats.
Recruiting Insiders
Similar to traditional targeted attacks by external threat actors, attacks harnessing insiders are often carried out over time, with the insider usually taking steps to hide their activity and remain undetected. They are attractive to threat actors because they have a high impact and are relatively low-cost to execute. They affect organizations of all sizes and industries because insiders are, by definition, those we normally trust. Contract staff, IT admins, individual contributors, lawyers, academics, and senior executives whether they be third-party contractors, current or past employees could all play the role of a malicious insider.
There are two common groups that criminal organizations gravitate towards:
- The first group has a lot of privilege with regard to access or managing systems, as such they are highly attractive to threat actors.
- The second group is motivation oriented. Typically, call center employees or retail staff are targeted here due to a lower wage bracket. The offer of earning an extra $1,000 or $2,000 in exchange for customer records can be very compelling, especially when economic conditions are tough.
It can be very difficult to predict human behavior. It is very rare that when somebody joins a company, they intend to become an insider. Employees can be persuaded to work on behalf of a threat actor as a result of cultural change or a change within their own personal circumstance that causes them to switch focus. While some individuals can be motivated by greed, anger, or ideology, this is not always the case.
When recruiting insiders, threat actors use various tactics. They can use blackmail and coercive techniques to extort the information they need from an employee, but from our findings, the majority of insiders on the dark web are recruited by financial rewards.
In most cases, threat actors will want to keep the number of observables to a minimum and enable remote access as quickly as possible. This makes it easier to recruit an insider and minimize the risk of getting caught.
Most targeted industries
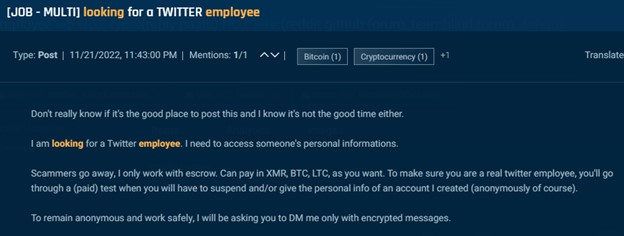
Our investigations found hundreds of posts on underground forums and Telegram during the past year, in which actors sought malicious insiders across many industries and for a variety of purposes. These include some of the world’s largest companies such as Amazon, Meta, Walmart, Chase, PayPal, AT&T, and Verizon.
While not all postings state the desired function of the insider, the ones that do fall into the following broad categories (roughly ranked from most to least common):
| Target industry | Function of malicious insider |
| Telecom | SIM swapping, credentials, customer data |
| Retail | Refund fraud, providing customer data, theft of goods |
| Shipping and logistics | Tracking scans, theft of packages |
| Social media | Banning, unbanning, and verifying accounts, providing customer data |
| Financial services | Approving transfers and withdrawals, account loading, currency exchange, server access |
| Government and military | Providing classified intelligence, citizen data |
This order of industries is interesting. In general, financial services are the most targeted industry on the dark web, since actors are financially motivated. However, when it comes to insider fraud, financial services are far lower down the list. There are several reasons for this. First, bank employees have relatively higher salaries, and sanctions for fraudulent activities are far more severe, so they might be less inclined to risk termination and legal action.
Second, because the stakes of fraudulent financial transactions are higher than, for example, retail fraud, banks invest considerably in vetting employees and embedding anti-fraud measures, such as requiring multiple sign-off on some transactions and automated flagging of suspicious activities.
However, a single instance of retail or shipping fraud (such as claiming an undeserved refund on an iPhone) is often far smaller than a fraudulent banking transaction. Therefore, companies in these sectors might not have similarly stringent measures.
Insider Threats: Telecom Industry
Telecom is the most popular industry for which underground threat actors solicit insiders. The purpose is generally clear: telecom employees can facilitate “SIM swaps,” a tactic in which the attacker causes the victim’s phone number to be ported to a SIM card in their possession. Once the attacker controls the victim’s phone number, they can carry out a number of attacks, such as intercepting one-time passwords sent via SMS or taking over cryptowallets tied to the number.
Porting a phone number is a routine business procedure carried out by store employees. Thus, finding someone to execute an unauthorized port might be relatively easy: it could involve approaching an employee, offering payment, and even showing some fake IDs to grant plausible deniability.
There is a considerable quantity of underground posts discussing insiders for performing SIM swaps. In the image below an actor seeking an insider at a Verizon store to perform SIM swapping.

Cybersixgill
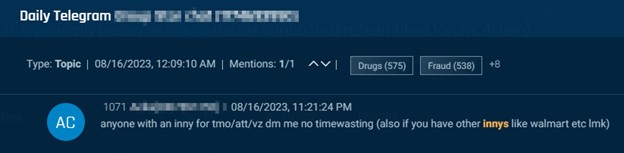
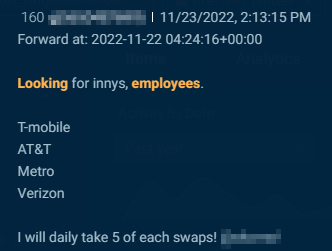
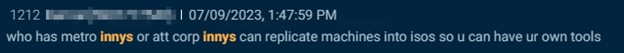
Telegram is the most popular venue for actors to seek telecom insiders, also referred to as innys. In the examples below, threat actors seek SIM swaps through insiders at organizations including T-Mobile, AT&T, Metro and Verizon.
Cybersixgill
Cybersixgill
Cybersixgill
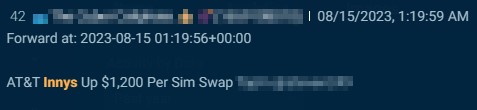
Occasionally, the post’s author will even state how much they will pay for swaps, such as this author (below), who offers $1,200 apiece.
Cybersixgill
This actor, who charges $2,000 per swap, offers proof of working with an insider, including a screenshot of AT&T’s employee portal and DMs with the insider.
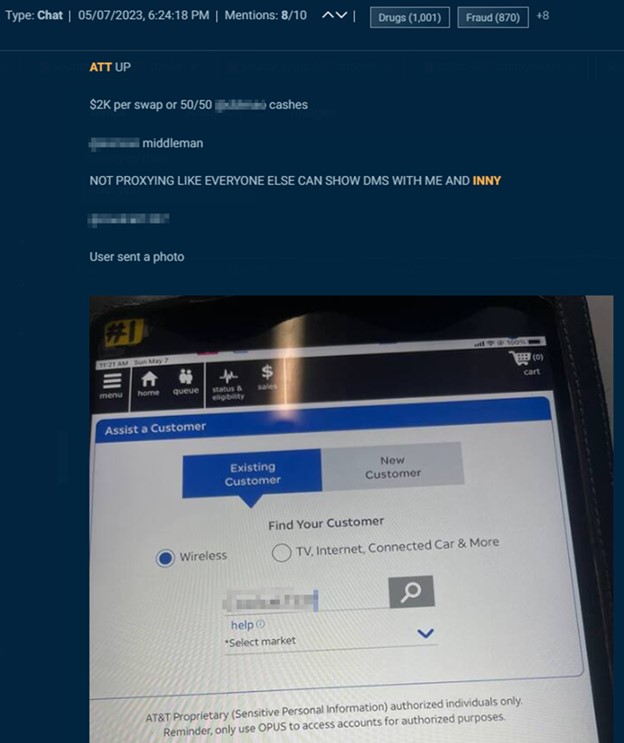
Cybersixgill
In addition to SIM swapping, underground actors also seek telecom insiders for credentials, customer data, and general information. In the images below you’ll first see an actor on an underground forum seeking Vodafone insiders to provide customer data. Then an actor seeks telecom insiders in Russia, Ukraine, Kazakhstan, Belarus, and Uzbekistan. Folowed by an actor that seeks a Claro Colombia employee to answer some questions.
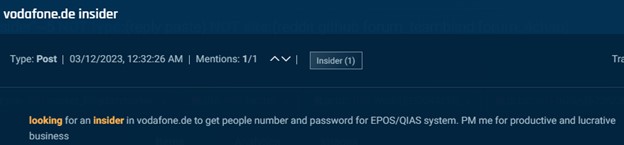
Cybersixgill
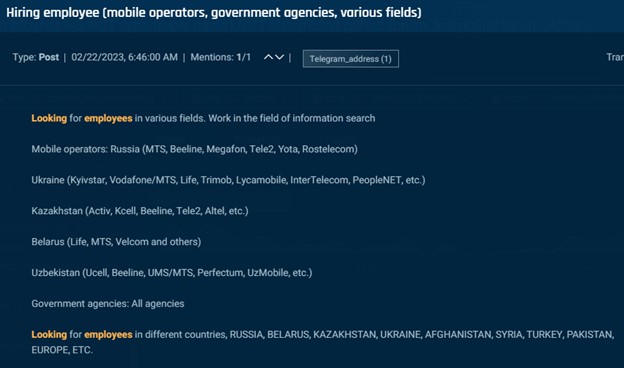
Cybersixgill
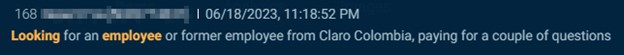
Cybersixgill
Sometimes we find insiders reaching out. For example, this self-described “disgruntled telecom employee” is offering to sell information regarding eSIMs, which will enable porting numbers with nothing more than running “a script in the cloud.”
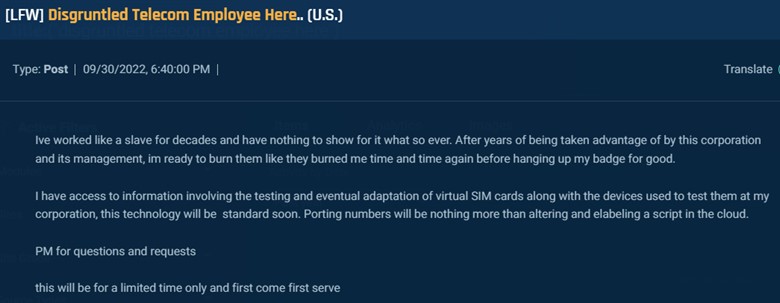
Cybersixgill
Insider Threats: Retail Sector
Underground threat actors typically seek retail insiders to receive goods for free. One common scheme in which they can involve insiders is refund fraud, also known as refunding, in which an actor claims undeserved refunds for a product.
There are many techniques to carry out this type of attack, including reporting that an empty box or damaged item arrived or returning an empty box. However, most methods require convincing an employee to accept the story; it is easier to carry out a fake return if they are already a willing accomplice.
Some threat actors state quite plainly that they are seeking insiders for refund scams. In the examples below, one actor offers $5,000 for an insider responsible for returns at Walmart or any other retailer, while another offers an undisclosed sum to insiders who work with them.
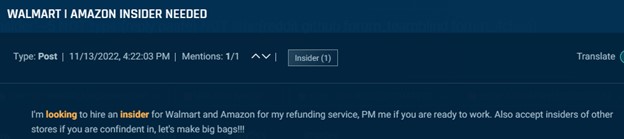
Cybersixgill
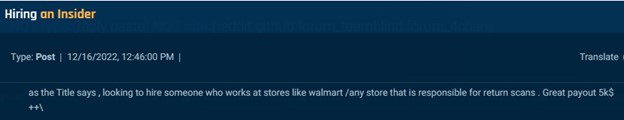
Cybersixgill
Other actors are not as explicit about wanting an insider to assist with refund scams. For example, the actor in the post below sought an Amazon insider, preferably a customer support supervisor. Someone in this role would be able to authorize returns.
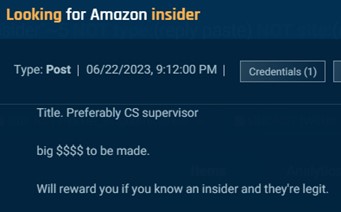
Cybersixgill
Threat actors also recruit insiders in e-commerce. For example, this actor seeks eBay insiders who can unblock suspended accounts.
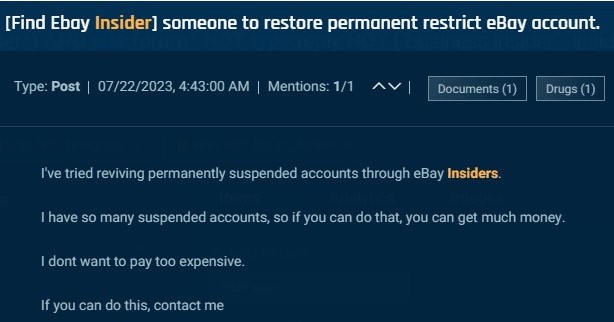
Cybersixgill
Another actor persistently sought insiders at lego.com to provide information about orders, posting eight times in two months.
However, in many postings, there are few, if any, clues about why an insider is requested, though we may presume that they are related to theft. One actor seeks an Amazon warehouse worker; another seeks an Amazon India employee who can assist with bulk orders, and another seeks associates at a long and varied list of companies to help with “customer lookups,” to provide sensitive and confidential customer data.
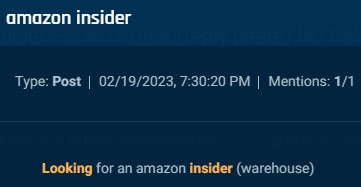
Cybersixgill
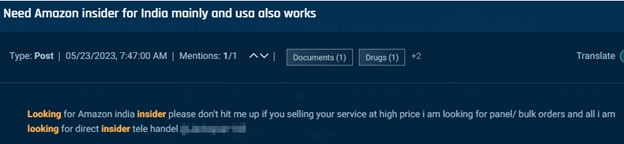
Cybersixgill
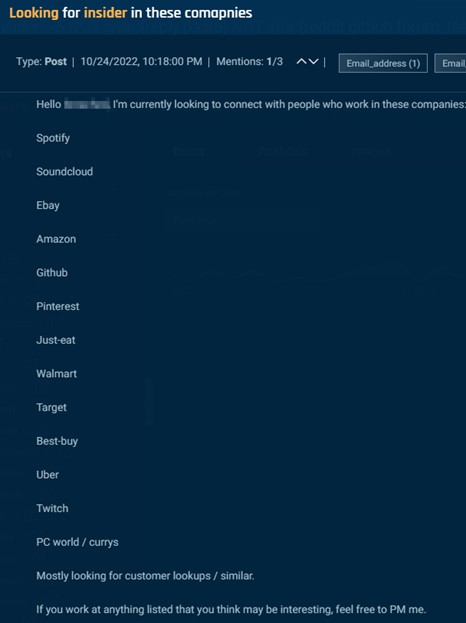
Cybersixgill
Insider Threats: Shipping and logistics
Underground threat actors recruit insiders in shipping and logistics primarily to execute fraudulent tracking scans. Just like in the example below where an actor seeks an insider at UPS and other couriers to perform scans.
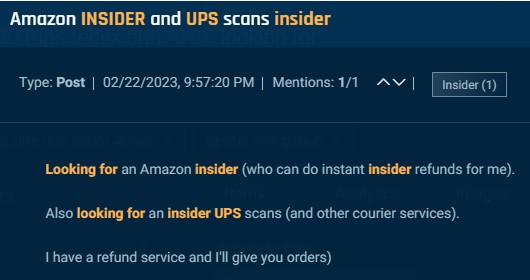
Cybersixgill
Insider scans are another technique in refund scams. In this scheme, an actor requests to return an item to an e-commerce store. An accomplice in the shipping company scans the shipping label, confirming to the retailer that the item is in transit. The retailer issues a refund but never receives the package. Fraudsters can also use insider scans and courier insiders to simply “ship” a package that disappears, allowing them to claim insurance for their losses.
The examples below show how malicious actors go about performing these scams. In one image an actor seeking insider scans at UPS, DHL, and other carriers to assist with refund scams and in the following an actor looking for employees at UPS, FedEx, USPS or other couriers.
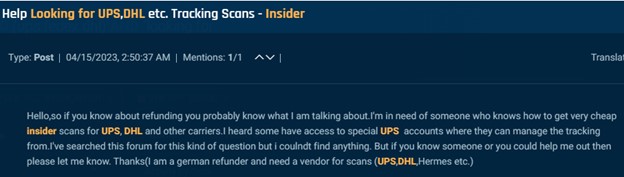
Cybersixgill
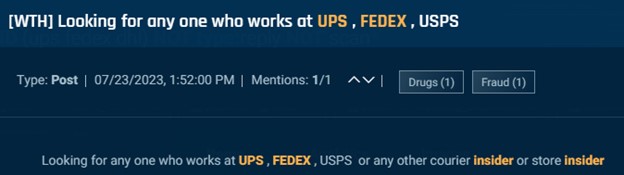
Cybersixgill
Many posts recruiting courier insiders, such as the example below, offer “big money” to malicious employees.
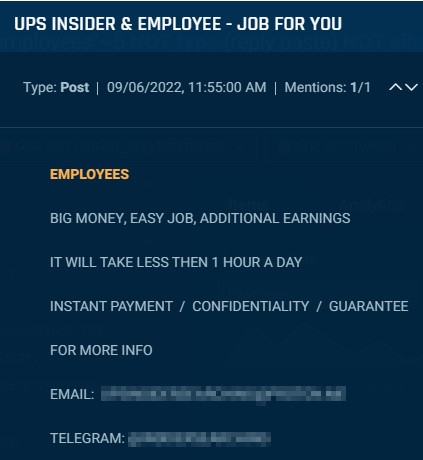
Cybersixgill
Others offer insider scans as a service such as the post below, requesting $60 per scan at FedEx, UPS, Royal Mail, and other couriers.
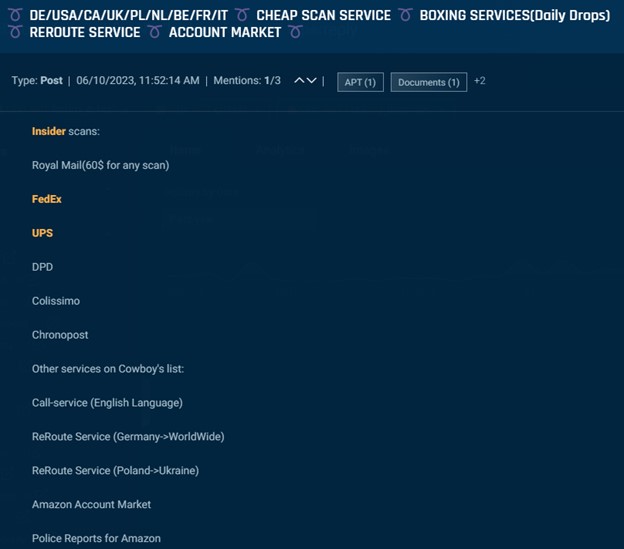
Cybersixgill
Insider Threats: Social media
Threat actors target insiders at social media companies to ban, un-ban and access customer data. The examples below show how one actor on Telegram claimed to be “paying good” for someone at Instagram or X (formerly Twitter), and another offered “$$$$$$” for someone at Snapchat.
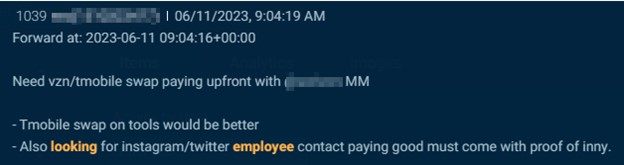
Cybersixgill
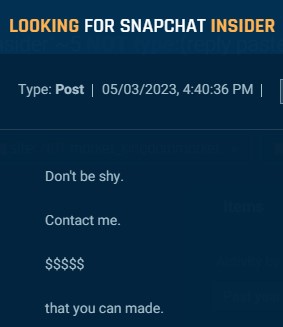
Cybersixgill
If the post specifies the function of the desired insider, it generally has to do with banning, unbanning, or verifying accounts. In addition to this, actors also seek social media employees to provide a user’s personal information.
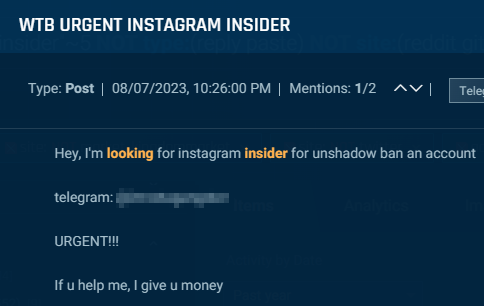
Cybersixgill
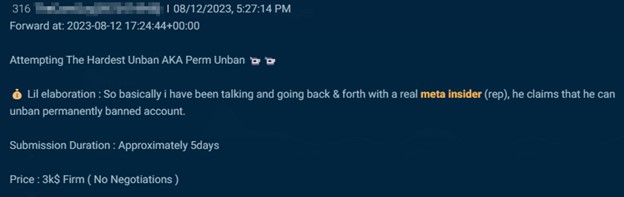
Cybersixgill
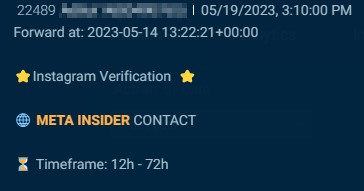
Cybersixgill
Cybersixgill
Insider Threats: Financial services
An insider at a bank or other financial services company might be the necessary link to execute a large, fraudulent scheme. Underground actors use insiders at banks to approve payments and money transfers, enabling fraudsters to move and launder money. In the next example, an actor claims to have an insider at Metro, Santander, and Barclays that can approve payments of up to GBP90,000-GBP200,000 (depending on the bank). The actor notes that these payments appear legitimate and do not burn the account.
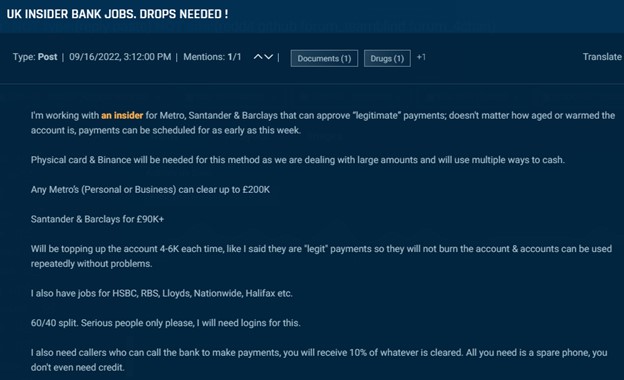
Cybersixgill
In this next example, an actor claims to have a Bank of America insider onboard. The actor is seeking account and routing information, as well as mobile phone numbers, in order to carry out their scheme.

Cybersixgill
Insiders also allegedly assist with “loading,” an activity involving moving money to an account in the actor’s control.
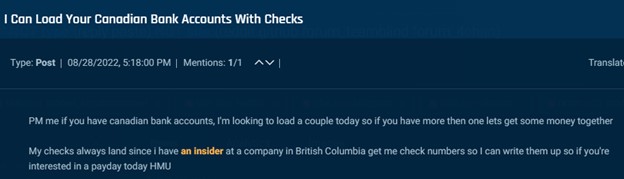
Cybersixgill
Similarly, actors seek to use insiders for money conversions. The example below is from an actor expecting to receive $10,000-$30,000 each day from a “project” and seeks a PayPal employee to convert it into cryptocurrency.
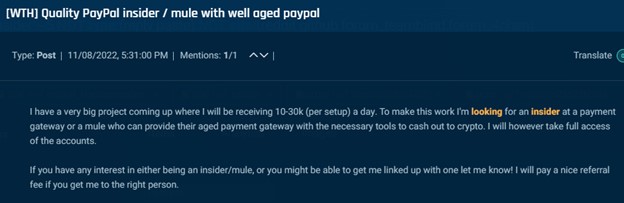
Cybersixgill
Actors also seek bank insiders with access to the SWITCH application server.

Cybersixgill
In this next post, the actor even notes that they seek to deploy the FASTCASH malware. FASTCASH malware can be used to cause ATMs to eject their cash, and it was originally identified with Hidden Cobra, a North Korean advanced persistent threat (APT). Whether these posts’ authors have any connection to the group is uncertain, however, if they succeed in gaining access to the SWITCH application server, they stand to generate very significant cash payouts.
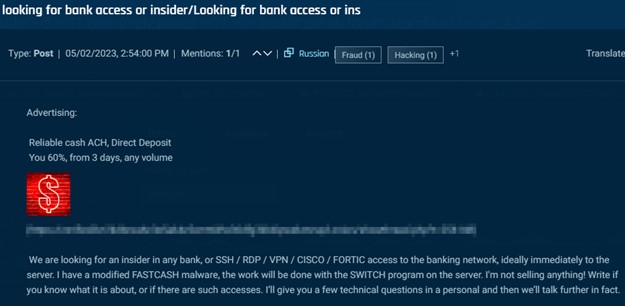
Cybersixgill
Insider Threats: Government and military
Transcending from cybercrime to espionage, we discovered several posts in which actors solicited governmental or government-affiliated insiders to provide information. This includes individuals, like in the image below, who can provide national citizen databases to assist in doxing. An actor seeking an insider in the French government to provide citizen data.
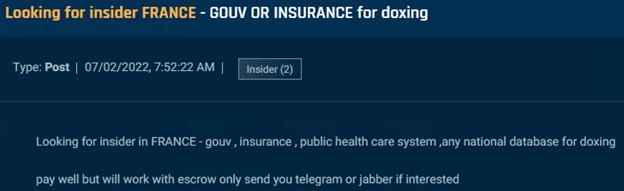
Cybersixgill
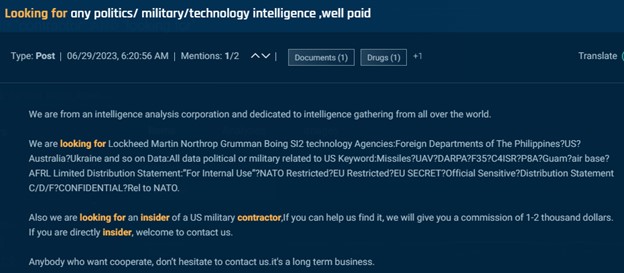
Other posts seek individuals who can provide classified information. For example, this next post appeared several times across several forums and Telegram from a self-described “intelligence analysis corporation” offering $1,000-$2,000 as a finders fee for someone that can connect them with an insider at a US military contractor.
Cybersixgill
Finally, we also discovered the below post in which an individual purported to sell sixteen sets of classified government data, including proprietary data belonging to defense manufacturers such as Raytheon and Elbit. The post also lists a secret document about a confidential Five Eyes military exercise for $300, noting that it was obtained by an insider.

Cybersixgill
We must emphasize that posts soliciting insiders to provide classified information are rare. The penalties for such activities are severe, and most of the dark web’s users are financially motivated. Even so, it is not unheard of for an insider to leak classified information on the deep and dark web; most recently, a Massachusetts National Guardsman has been charged with posting classified documents on a Discord server.
Defending Against Insider Threats
Employees can pose a unique type of threat to an organization. Most employees are not malicious, and they ought to be trusted with access to the data and systems needed for performing their tasks. However, those who are lured by a variety of methods to use their positions to assist in criminal enterprises can cause significant financial and reputational damage to their employers.
According to the 2023 Verizon Data Breach Investigations Report, malicious insiders perpetrate about 19% of known data breaches. While there is no way of knowing for sure how many of these attacks originated from a partnership forged on the deep and dark web, there are several practices that companies can take to protect themselves.
- Principal of least privilege: Employee privileges should be limited only to what their tasks require.
- Job rotation: Regular cycling of employees between tasks to reveal fraudulent activity.
- Multiple signoff: Execution of sensitive actions should require multiple employees to approve.
- VIP account protection: Customers with sensitive accounts or who are more likely to be targeted should be able to opt-in to more stringent account protection.
- Employee awareness: Employees should understand that threat actors seek to recruit their peers and perpetrate fraud. If they see something suspicious, they should report it.
- Automated detection: Use of software to flag suspicious activities.
- Underground monitoring: Organizations must understand adversarial efforts to recruit insiders. Real-time cyber threat intelligence from the clear, deep, and dark web is essential to gather the information needed to expose organizational risk from insider threats.
A rogue employee can severely impact a business’s operations, finances, network security, and brand. They are far more than just an “IT problem” or even a “security team problem.” A proper organizational defense requires coordination between technical and non-technical players, from the SOC to HR, in order to keep the company secure.
Organizations must identify which of their employees are in roles that might be targeted for recruitment by cybercriminals, and enforce stringent monitoring and controls to neutralize any threats from inside the building.
